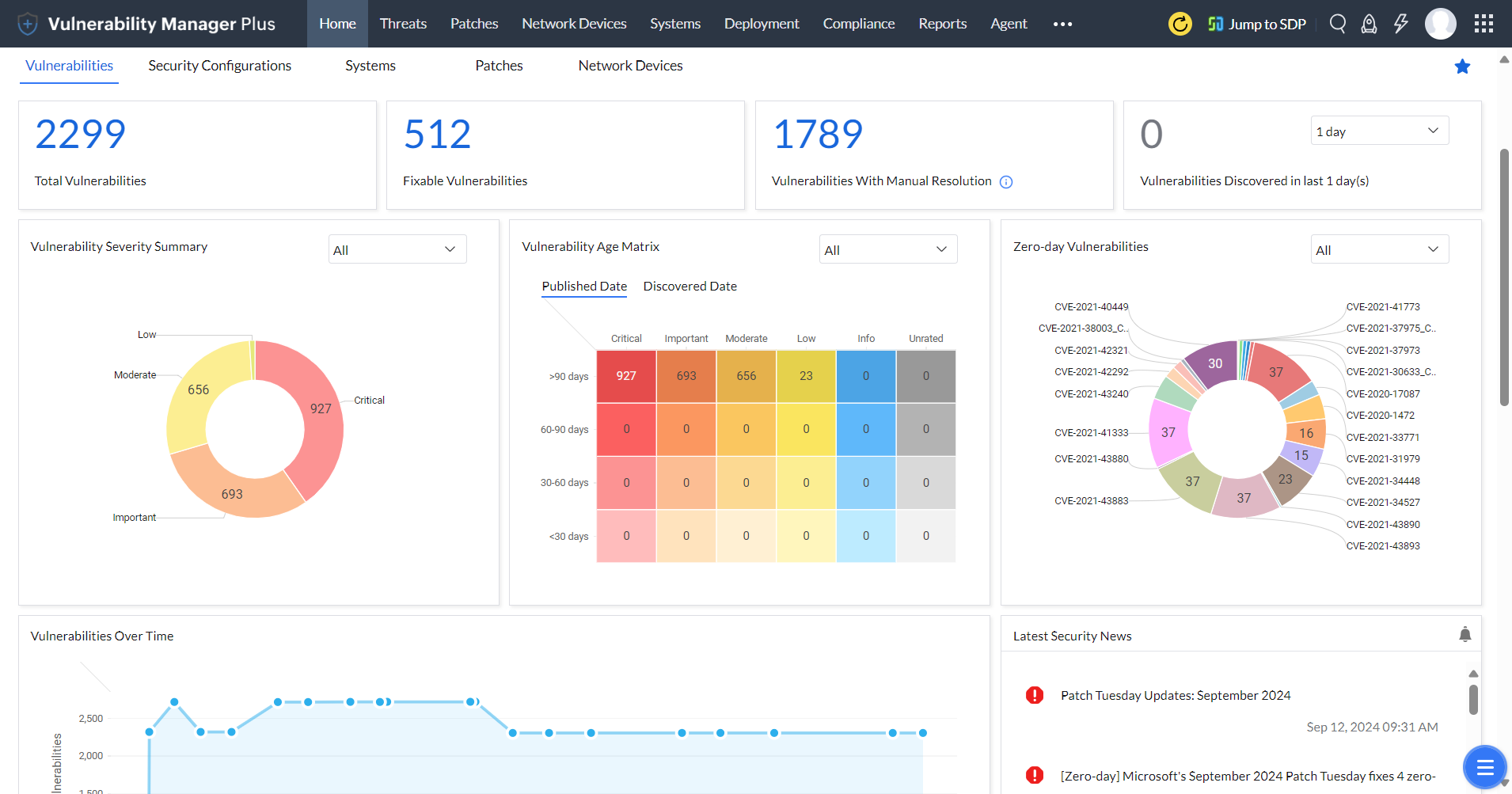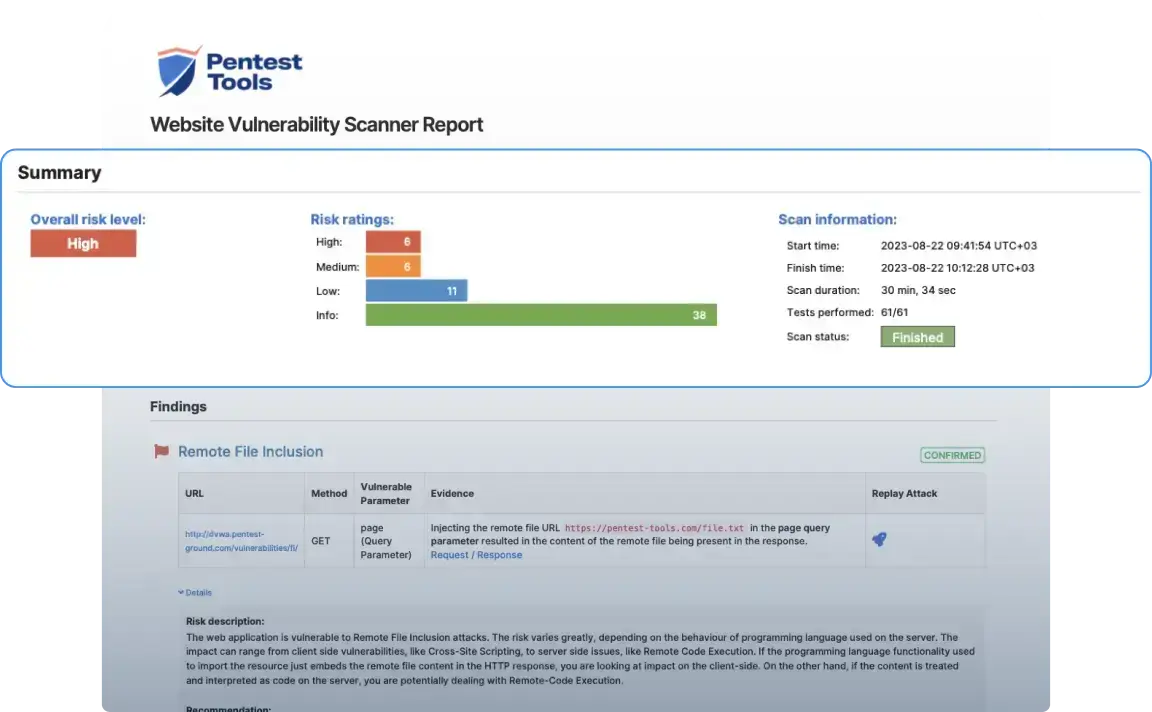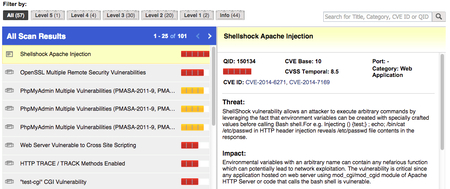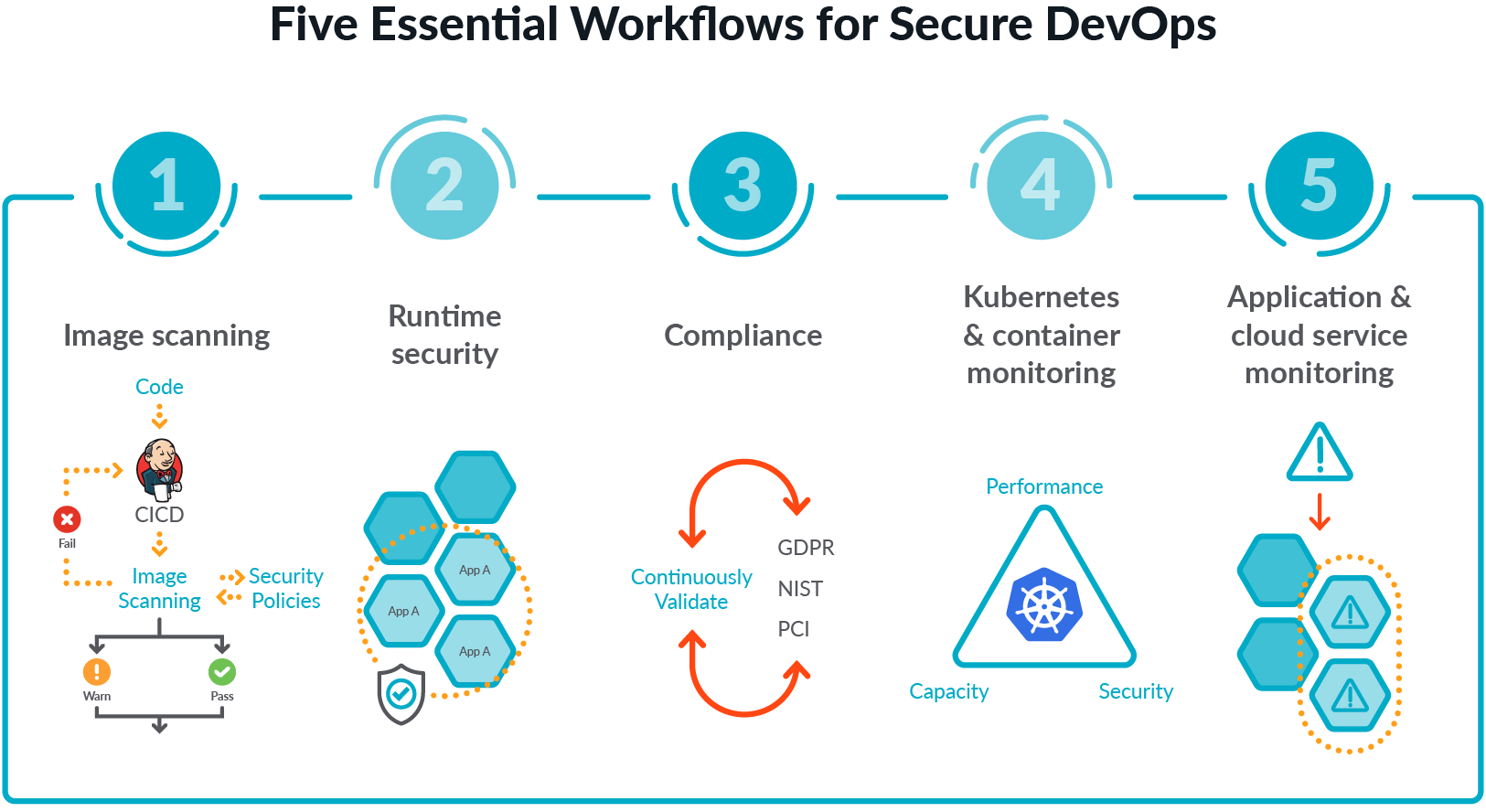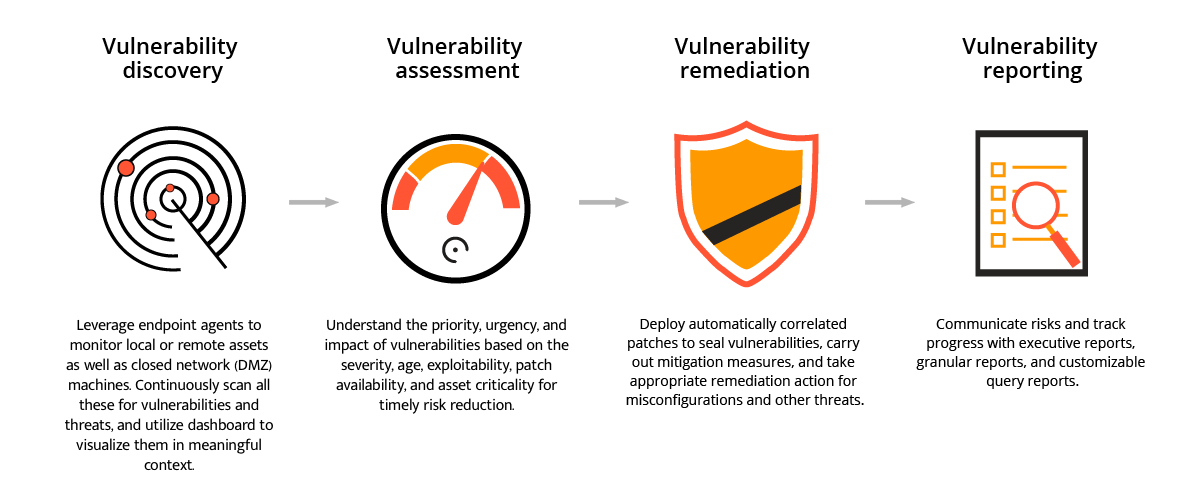
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
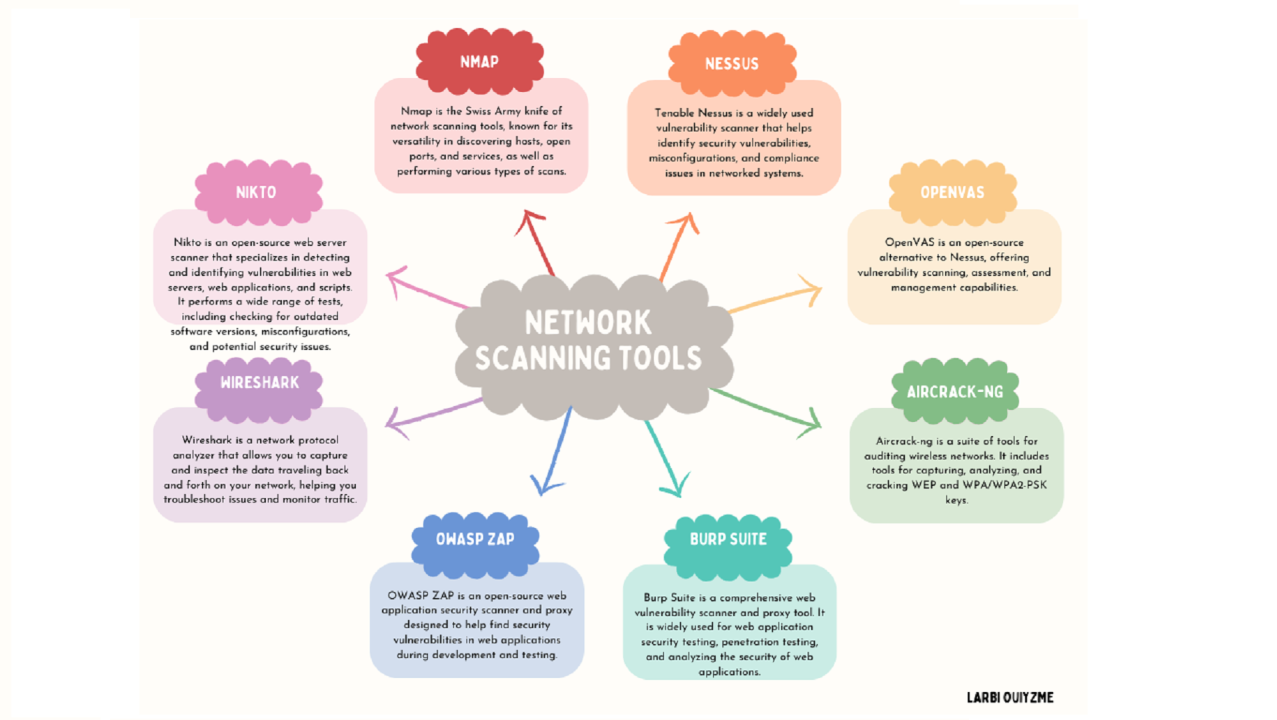
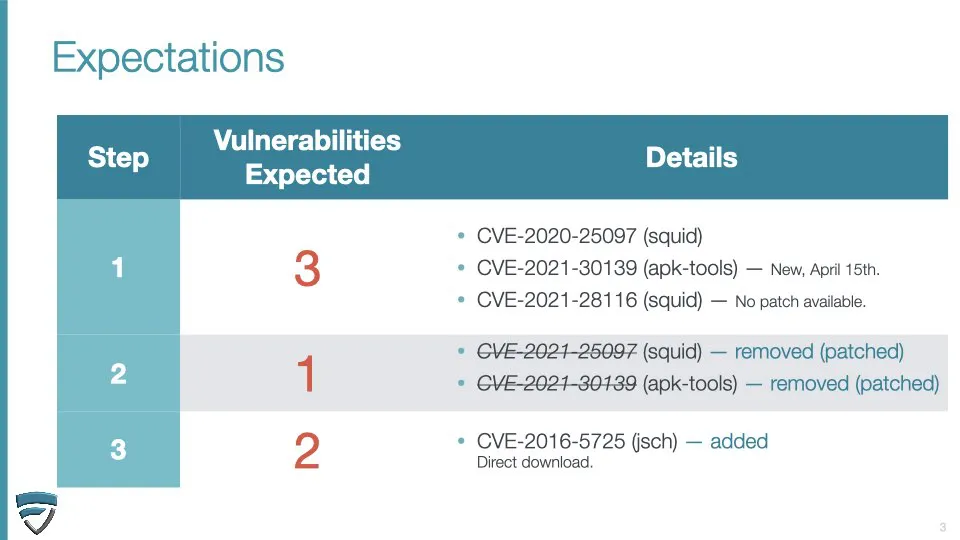
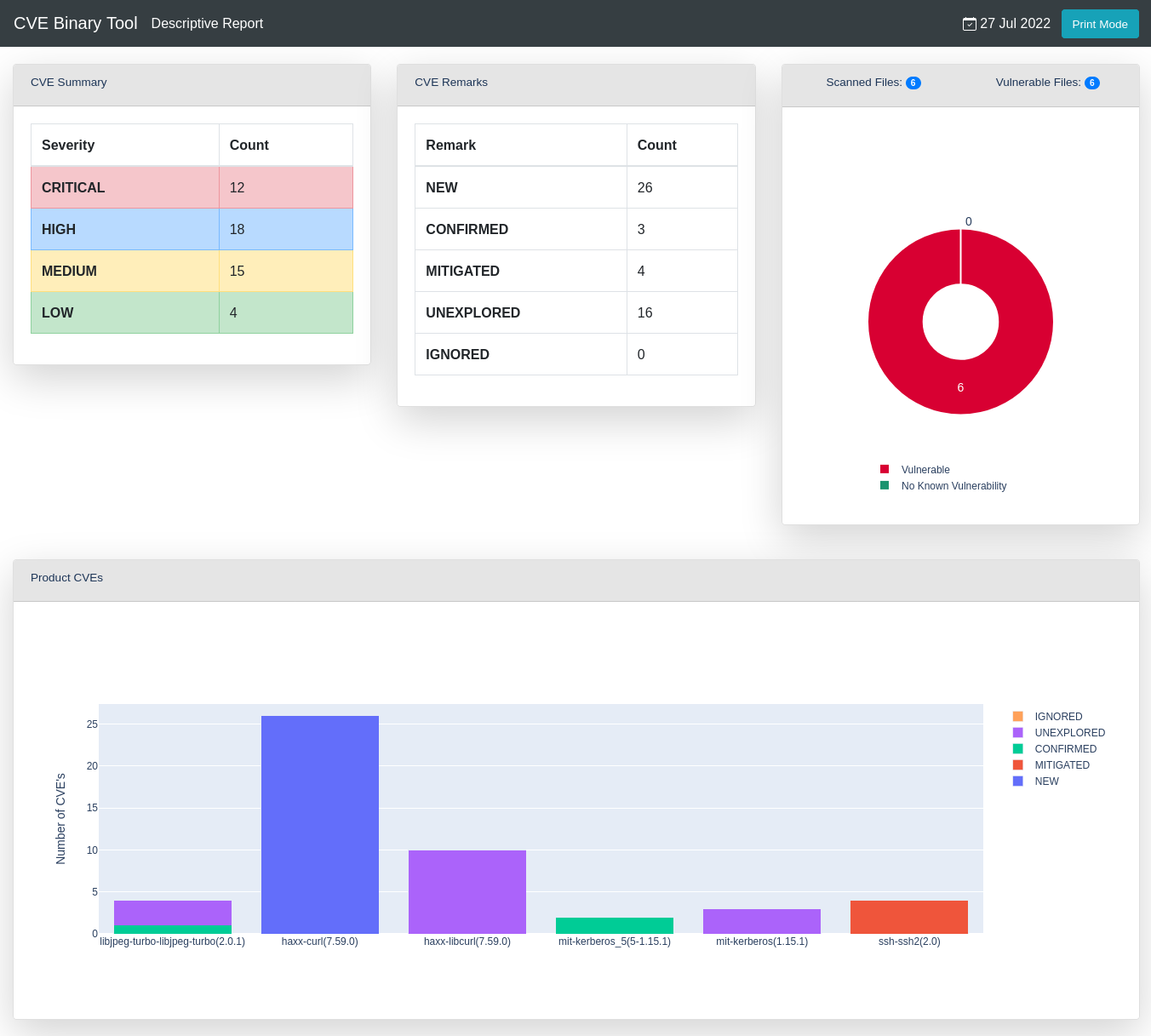
GitHub - intel/cve-bin-tool: The CVE Binary Tool helps you determine if your system includes known vulnerabilities. You can scan binaries for over 200 common, vulnerable components (openssl, libpng, libxml2, expat and others),

Harun Seker, CISSP on LinkedIn: #cybersecurity #vulnerabilitymanagement #vulnerabilityassessment… | 28 comments
GitHub - vulncheck-oss/cve-2023-36845-scanner: A tool to discover Juniper firewalls vulnerable to CVE-2023-36845