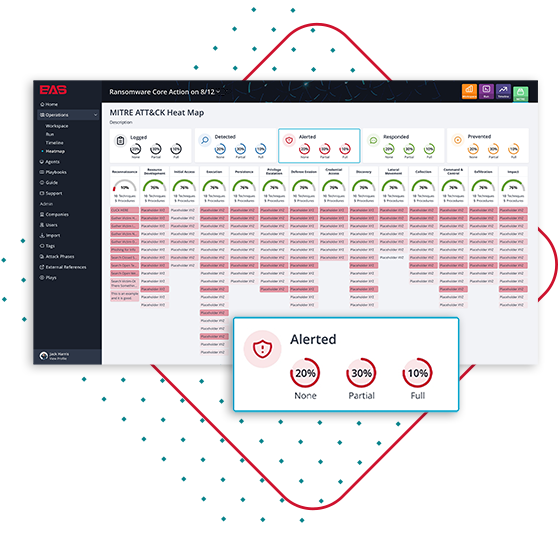
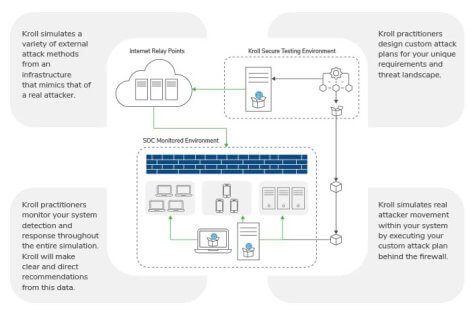
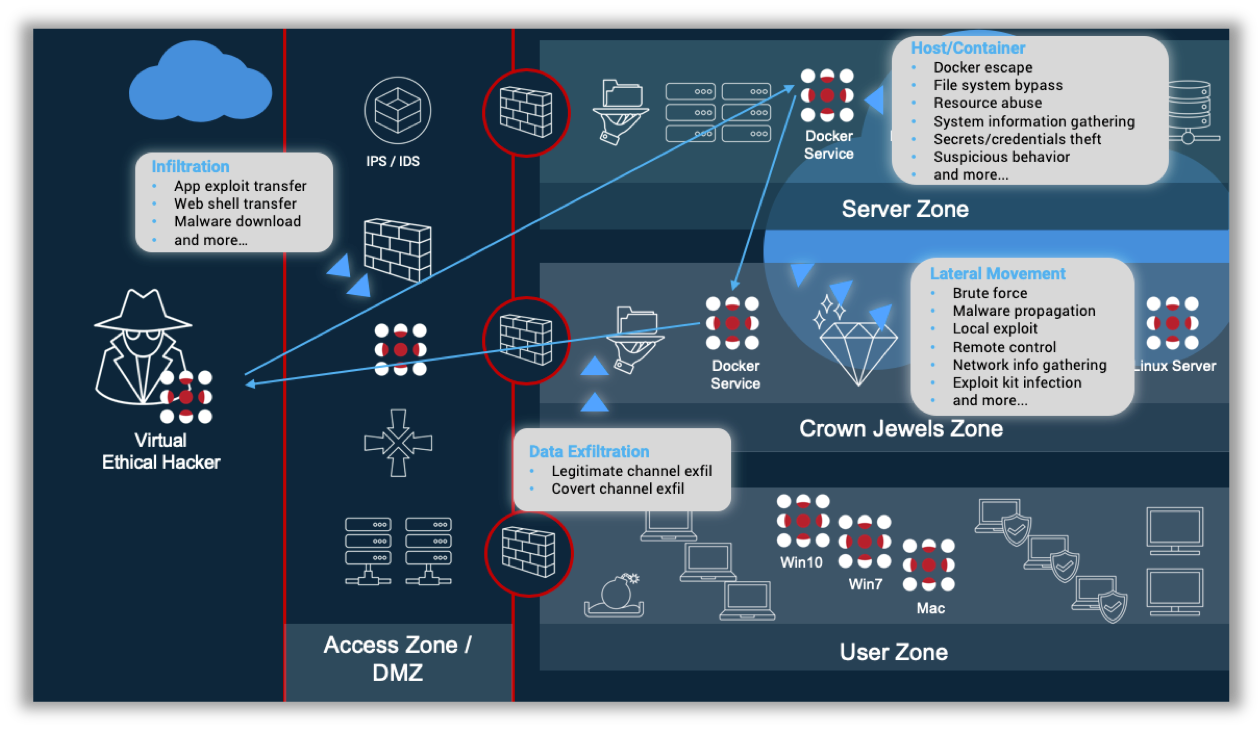
Breach and Attack Simulation Tools Market Customer Insights, Statistical Data Solutions With Research Analysis Globally
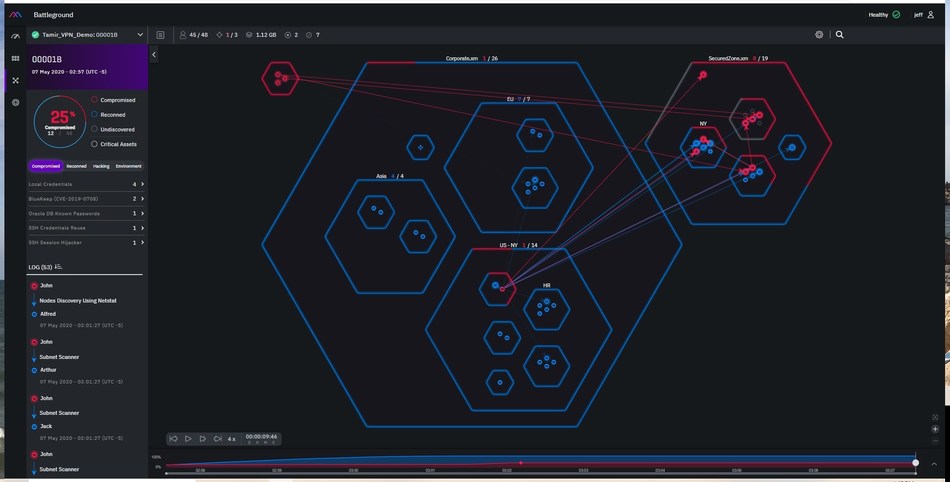
New Research Shows that Breach and Attack Simulation Technology is Key for Managing Cyber Risk in a World of Growing Complexity
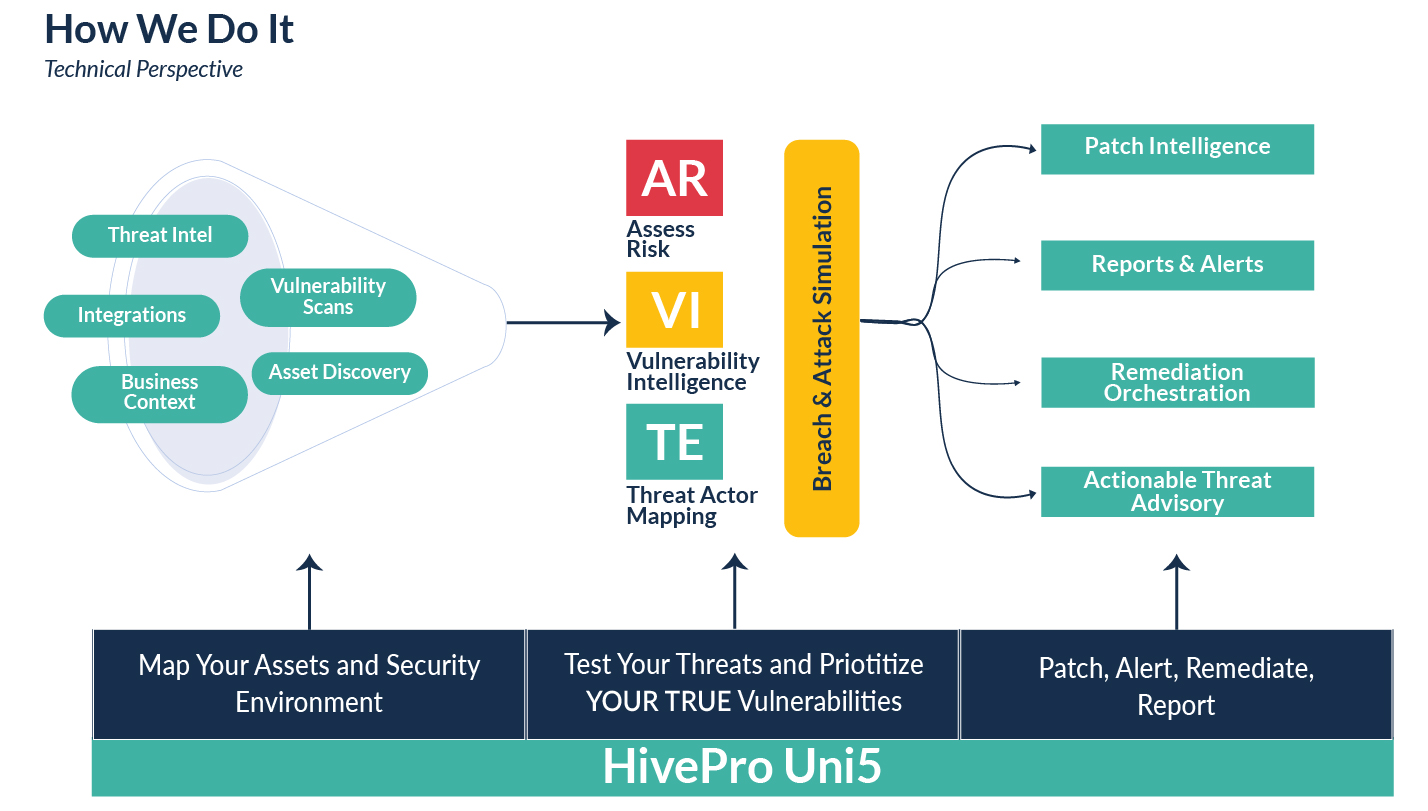
Hive Pro includes Breach & Attack Simulation as a feature in its Threat Exposure Management Platform- Hive Pro Blogs